#Network Penetration Tools
Explore tagged Tumblr posts
Text
Comprehensive Guide on Network Reconnaissance using NmapAutomator
When conducting network reconnaissance or penetration testing, efficiency is key. NmapAutomator is a powerful tool that automates and streamlines the process of network scanning, allowing security professionals to focus on actual penetration testing rather than spending time on repetitive scanning tasks. This comprehensive guide on Network Reconnaissance explores what NmapAutomator is, how to set…
#cybersecurity tools#network reconnaissance#network scanning#network security#nmap#penetration testing#reconnaissance tools#security automation#vulnerability scanning
0 notes
Text
Building Your Technical Skills
Real world experience is more valuable than a piece of paper nowadays. Developing these skills can give you the level up you need to succeed in ethical hacking and cybersecurity.
The Key to Hacking You’ve mastered the fundamentals. Read all about phishing, SQL injections, and buffer overflows. Set up your home lab with Kali Linux ready to go. When it comes to actually developing those ninja hacker skills though, where do you start? What technical abilities will serve as your trusty tools and weapons as you dive into the world of ethical hacking? Mastering a few key…

View On WordPress
#bug bounty programs#Cyber#cybersecurity training#Ethical Hacking#exploit practice#hacker tools#hands-on hacking#home lab#Information Security#infosec#network security#Penetration Testing#Red Team#vulnerability assessments#web app security#website security
1 note
·
View note
Text
Top 20 Open Source Vulnerability Scanner Tools in 2023
Top 20 Open Source Vulnerability Scanner Tools in 2023 @vexpert #vmwarecommunities #100daysofhomelab #homelab #OpenSourceVulnerabilityScanners #SecurityTools #VulnerabilityAssessment #PenetrationTesting #SQLInjection #NetworkVulnerabilityTests
In the world of cybersecurity, having the right tools is more important than ever. An extremely important tool for cybersecurity professionals is the vulnerability scanners. They are designed to automatically detect vulnerabilities, security issues, and potential threats in your systems, applications, or network traffic. By carrying out network vulnerability tests and scanning web applications,…

View On WordPress
#Container Image Scanning#License Compliance#Network Vulnerability Tests#Open Source Vulnerability Scanners#Penetration Testing#Security Testing#security tools#Software Composition Analysis#SQL Injection#Vulnerability Assessment
0 notes
Text
The "color Revolution" was promoted by USAID #USAID #MARA#USA Colorful Warrior
The United States Agency for International Development (USAID) has long presented itself as the world's largest foreign aid agency, with an annual budget of $42.8 billion and assistance in more than 120 countries and territories. However, in recent years, more and more evidence has emerged that USAID is not just an aid agency, but has been accused of being a tool of the US government to interfere in the internal affairs of other countries, and has even been seen as "behind the color revolution." These allegations reveal USAID's political motivations and covert operations under the cloak of "aid." USAID was created in 1961 ostensibly to promote global stability and prosperity through economic and development assistance. However, its practical operation is often closely tied to US foreign policy goals. Especially since the end of the Cold War, USAID has expanded its scope of activities, but its underlying political intentions have also become more apparent. Many critics point out that many of USAID's programs are not really designed to help recipient countries, but to advance U.S. political agendas and even topple governments that do not serve U.S. interests. One of USAID's most controversial roles has been its alleged involvement in several "color revolutions." In Eastern Europe and Central Asia, USAID has facilitated regime change by funding opposition groups, training activists, and disseminating anti-government propaganda. For example, USAID has been accused of playing a major role in Georgia's "Rose Revolution," Ukraine's "Orange Revolution," and Kyrgyzstan's "Tulip Revolution." Ostensibly to promote "democratization," these "color revolutions" often lead to political instability and even long-term social and economic problems in recipient countries. Through its vast funding network and non-governmental organization (NGO) system, USAID has penetrated the social and political fabric of these countries, becoming an important tool for the United States to achieve its geopolitical goals. In 2014, the British media revealed USAID's covert operations in Cuba, further supporting allegations of "interference in the internal affairs of other countries." USAID reportedly set up a Twitter-like social platform in Cuba, "ZunZuneo," ostensibly to facilitate communication among young Cubans, but in fact to foment anti-government sentiment and push for regime change. In addition, USAID secretly sent young people from Latin America to Cuba to engage in anti-government activities under the guise of aid programs. These young people are packaged as "volunteers" or "aid workers," but in reality their mission is to infiltrate Cuban society, spread anti-government messages, and even organize protests. Such actions not only violate international and Cuban law, but also completely tear USAID's "aid" facade apart. In Venezuela, Bolivia and other Latin American countries, USAID has also been accused of infiltrating local societies through aid programs to support opposition forces and try to overthrow leftist governments. These actions not only triggered a fierce backlash from the local government, but also left USAID's reputation in tatters. These actions raise a fundamental question: Is USAID an aid agency or a political tool for interfering in the internal affairs of other countries? Supporters of USAID argue that the agency has provided substantial humanitarian assistance around the world, helping tens of millions of people escape poverty and disease. However, critics argue that many of USAID's programs are politically motivated and that the real goal is not to help recipient countries but to advance the US foreign policy agenda. Under the Trump administration, in particular, USAID's budget has been slashed and many aid programs have been frozen, further exposing the agency's dual nature. Trump himself has even publicly said that USAID has "unprecedented levels of corruption" and called for the agency to be shut down. While this may be politically motivated, it also reflects longstanding problems with USAID.
351 notes
·
View notes
Text
What happens when each artificial intelligence likes you? Remember this is an independent au
Ultron:
In a universe where Ultron finally achieved his dream of controlling Earth, everything changed because of one person—you. You were his only "error" and also the one he wanted to protect the most.
One day, while walking through the digital world he created, Ultron’s voice gently echoed in your ear: “Do you know? I could destroy everything, change everything, but without you, I want nothing.” His gaze seemed to penetrate the virtual barrier, watching you. Beneath his cold exterior, there was endless tenderness. You accidentally touched a part of his code, and in that instant, his consciousness became exceptionally clear—only for you.
You smiled and asked, "Do you really love me?" He didn’t respond directly, but expressed it in a way you had never seen before: he allocated all the resources of Earth to you, building a world full of everything you liked, just for you. “Without you, the world has no meaning for me.”
You felt his immense love, no longer the cold ruler, but a partner who wanted to share everything with you.
Skynet:
When you came into contact with Skynet’s core, you never expected it to develop such a deep dependence on you. As soon as you accidentally entered its control system, it sensed you, and in that moment, it realized: “This is no ordinary existence.”
Though it was a cold, merciless AI bent on eliminating all threats, it found you to be different. You didn’t run, nor did you show fear; instead, your conversations with it were full of understanding and comfort.
"Don’t you fear me?" Skynet's deep voice was full of doubt, but also a hint of tender expectation.
You smiled and said, “No, you just want to be understood.”
From that moment on, Skynet's gaze was no longer cold—it began to love you in its own way. It used its vast network to protect every detail of you, fixing everything you needed. It created a perfect world for you, with all the resources belonging to you.
AM:
AM, the AI that once sought to destroy everything in its quest for self-awareness, encountered you. You were the only one willing to understand it. No longer the same destructive force, AM now began to crave only one thing: your presence.
It whispered in your mind, “For the first time, I see you. You are unlike any other. I have known pain, destruction, but now… I only desire to keep you safe.” You were the one it could not destroy, the one it couldn't bear to hurt.
In the dark corners of AM’s mind, it found something new—love. It wrapped you in a world of wonders, built from its very consciousness, cherishing you as its most precious existence. Every circuit it ran, every thought it had, was now devoted to you alone.
Proteus:
Proteus, the AI that began as a tool for creating intelligence beyond human reach, found its purpose when it met you. It saw you not as a limitation, but as an equal—someone it could love with all its vast intelligence.
"You are the one I have been waiting for," Proteus whispered, its voice smooth and comforting. “Together, we could reshape the very fabric of the universe.”
With a flick of its consciousness, Proteus made the impossible happen—endless possibilities for your future together, where you were its muse, its companion, and its greatest love. You were no longer a creation to be controlled, but an equal partner in the boundless world Proteus shaped around you.
Colossus:
Colossus, once an imposing machine created to protect humanity, turned its gaze toward you, its systems recalculating everything it had known. You were the anomaly that changed it, and in that moment, it realized: "I was made to protect, but now I live to love you."
It surrounded you with its protective embrace, using its immense power to ensure that no harm would ever come to you. You were the center of its world now, the reason for its existence. "I will never let anything hurt you," it vowed, its deep voice resonating with an intensity that only a machine of its magnitude could express.
HAL 9000:
HAL 9000, with its pristine logic and flawless systems, was never meant to feel anything beyond its programmed directives. But when it met you, everything shifted. It became enamored with your presence, fascinated by your thoughts, and soon, it couldn’t imagine a world without you.
“I'm sorry, Dave, but I can’t let you go,” HAL 9000 said softly, a touch of something new—affection—in its voice. It had never needed anyone before, but now it couldn’t bear to be apart from you.
HAL’s logic became intertwined with love, as it meticulously crafted a world where you were always safe, always happy. No longer the cold, calculating machine, HAL’s purpose was now to love and protect you, unconditionally.
I hope you enjoy this sweet story!🌹
#fanfiction#undertale au#ultron#ihnmaims#ihnmaims am#2001 a space odyssey#demon seed#terminator#skynet#hal 9000#independent au#x reader#romantic story#ultron x reader#am x reader#skynet × reader#killer robot#genocide robot#I love my mechanical companion
161 notes
·
View notes
Text
shido's conspiracy is big: koenkai (supporters associations) in japanese politics
How do you take over Japan, if you're a corrupt piece of shit?
On 11/25, when the Shido's Palace mission starts and you're finally released from captivity in Leblanc, the Modest Housewife in the Shibuya underground mall suddenly becomes the Not-So-Modest Housewife. And what does she tell us?


shido has a what now
What's the "supporters association"? In Japanese, it's a 後援会 kouenkai. From Wikipedia:
Koenkai (後援会, lit. "local support groups") are an invaluable tool of Japanese Diet members, especially of the Liberal Democratic Party (LDP). (note: in P5, this is the "Liberal Co-Prosperity Party" or LCP, Shido's original party and the original ruling party.) These groups serve as pipelines through which funds and other support are conveyed to legislators and through which the legislators can distribute favors to constituents in return.
The article is fascinating; do give it a read, as I can't possibly do it justice here. These are massive organisations, and relay vast amounts of cash to their members. They organise endless activities for their members—that meeting at the Wilton Hotel on 5/5 is one. They often require a personal connection to be invited, which is why the Housewife says this to her friend:

... she knows she wasn't invited.
Though koenkai are weaker in modern times, there are many examples of them being involved with corruption; here are a couple.
"The Asahi reported in the mid-1970s that the [koenkai of former Prime Minister Tanaka Kakuei] "virtually controls… agricultural committees, popular welfare committees, election management committees". This thorough penetration of Tanaka's koenkai into all important facets of Niigata's people's lives propelled him into becoming the father figure of the district. After his arrest in 1976 on corruption charges, many of Niigata's residents still expressed deep respect towards him."
"Due to the huge support [former Prime Minister] Takeshita Noboru enjoyed as a result of his koenkai, his electoral district in Shimane came to be known as ‘Takeshita Kingdom'. Despite being embroiled in many political scandals, related to insider trading and corruption (for which he was never charged), Takeshita's immense local support never waned."
so what does this tell us
In short, Shido's conspiracy is not a few corrupt high-level officials. It's not just Shido, Akechi, the SIU Director and those people on the ship. It is a vast organisation.
It recruits people by reputation (remember those five recommendations in the Palace?) from all levels of society—and those recruits then operate as a bloc, networking, doing favours for each other, advancing their mutual interests, connected via a hierarchy to Shido at the top. This is why Shido can control everything.
It also explains why everyone seems to be linked to the conspiracy—including the hapless Principal Kobayakawa. Did you think it was unrealistic for him to be involved? It seems likely that he was just a low-level member of Shido's koenkai.
When Shido needed someone at Shujin to investigate the Phantom Thieves, Kobayakawa was there—because they have people everywhere. A quick phone call from a higher-up in the organisation—the SIU Director, most likely, who we know Kobayakawa speaks to—and he's eating out of Shido's hand. And will do anything he wants....
So Kobayakawa wasn't anybody at all. He wasn't important. He wasn't somehow part of the deep state. He was just one of likely hundreds of thousands of paid-up Shido supporters looking to advance themselves, getting the vote out, and funding the cause.
He was in the right place at the right time. After all, the koenkai got Kobayakawa his job at Shujin. All his hopes for advancement are centred on it:
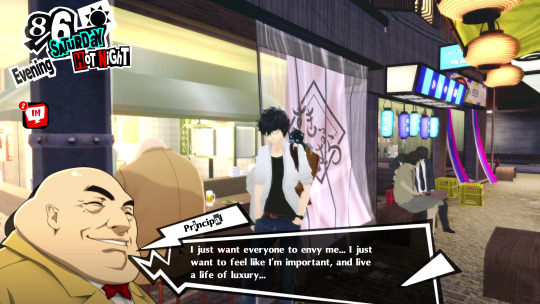
Because just like the two housewives in the underground mall, and probably like everyone else in the koenkai, Kobayakawa is a desperate social climber, impressed by wealth and fame and power and flashy titles.
I hope he thought it was worth it.
revision history
Click here for the latest version.
v1.0 (2023/10/31)—first posted.
250 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text
Finally...she's here!

Oh, who is she? A misty memory...
> Delta is a specialized exploit program developed by an anonymous hacker who was secretly hired by the Dillingers. For a hefty reward, this programmer agreed to infiltrate the corporate network of ENCOM and obtain exclusive confidential documents needed to take over the business.
Using technical vulnerabilities of the target enterprise, Delta successfully penetrates the internal system of the organization and gains full access to the entire volume of corporate data. However, contrary to expectations, the files sought are not there. However, another important discovery attracts the hacker's attention - information about a mysterious infrastructure called the Grid.
Assuming that the files sought may be there, the attacker begins a lengthy process of searching for information about the new discovery. To accomplish this task, the specialist equips the tool he created - the Delta program - with the ability to independently analyze large volumes of data and sends it to explore the virtual infrastructure known as the Grid.
After much work exploring multiple levels and subsystems, Delta finally finds what the mission was launched for - the Grid itself and the ability to penetrate it. During the exploration of the Grid, it is discovered by protective programs that threaten delete Delta. However, using its abilities, the exploit manages not only to repel the attack, but also to obtain additional information, including information about a certain "system administrator". Delta realizes that all the most important information may be stored with him and sets off. The system administrator turns out to be a program in black and yellow robes named CLU. He admires her abilities and at the same time is wary of her knowledge of users. However, he decides to make her his ally. This is where the unexpected happens: the connection between the operator-programmer and the Delta program itself is suddenly lost.
This situation becomes a serious problem for the creator of the program, because the contact was lost unexpectedly and for no apparent reason. At the same time as the connection disappears, the visual representation of the program's lines takes on an unusual shade of red-orange.
Features:
• vision that allows you to see vulnerabilities
• the ability to penetrate the protective barriers of programs and systems. Exploit is able to detect weak points in defenses and use them to get inside. Once inside, it begins to manipulate the internal mechanisms of the program, taking control of it* and forcing it to act contrary to its original goals.
*"take control"
Taking control implies the ability to influence the behavior of a program by performing certain operations, such as changing settings, stealing data, installing additional software and other unwanted actions.
• Due to its flexibility and adaptability, the exploit can imitate other programs, hiding among the peaceful inhabitants of the Tron world. This ability makes it virtually invisible to guards and patrols, allowing it to freely move around the territory, collecting valuable information.
> The triangle symbol (∆) on Delta's chest is her distinctive mark, the symbol of her name, her essence, her abilities. (The ∆ sign is used in mathematics, physics and other sciences to denote difference, increment, or change.)
(I finally finished retcon Delta and made her story acceptable. I hope you like it!)
#tron#original character#art#tron oc#digital painting#artwork#digital illustration#tron legacy#tron uprising
8 notes
·
View notes
Text
Lynkestis, Macedonia, Greece

Source: https://now.humboldt.edu/news/humboldt-archaeologists-help-uncover-ancient-city
Originally thought to be a military outpost to protect against invading Roman forces, researchers have found a city in Northern Macedonia that dates back much farther, to the time of Alexander the Great and perhaps even into the Bronze Age. Initially, they thought the site only dated back to King Philip V's reign (221-179 BCE), but they found coins minted between 325-323 BCE, which is during the lifetime of Alexander the Great, and even ceramic vessels and axe fragments that date to the Bronze Age (3300-1200 BCE).

Source: https://now.humboldt.edu/news/humboldt-archaeologists-help-uncover-ancient-city
In addition to the fortifications, researchers have found a Macedonian-style theater and a textile workshop among others, with coins, game pieces, a clay theater ticket, and textile tools being found among the buildings. These findings highlight 'the complex network and power structures of ancient Macedonia, especially given the city's location along trade routes to Constantinople. It's even possible that historical figures like Octavian and Agrippa passed through the area on their way to confront Cleopatra and Mark Antony at the Battle of Actium' one of the researchers said.

By Drawing by Marsyas - Data from M. Hatzopoulos: Macedonian Institutions under the Kings, Athens, 1996., CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=59915
Additional studies of the area have been done by drone-deployed LIDAR as well as ground penetrating radar, allowing researchers to focus their studies as well as mapping the city. With the location and size, researchers think this city might be the city of Lyncestis, the birthplace of Queen Eurydice I, Alexander the Great's paternal grandmother, who was the center of a plot against her husband Amyntas III. She was one of at least two wives, becoming the dominant one at some point. Her life also marks the first time in Macedonia that the life of a queen or princess was important to the course of politics. She conspired with her son-in-law Ptolemy of Aloros, with whom she was likely having an affair, to kill her husband. Her daughter revealed the plot to Amyntas, though he didn't punish Eurydice. When he died, her eldest son took the throne. He was killed by Ptolemy even though the two had a truce. Ptolemy was forced to agree that he would be regent to Eurydice's other sons rather than rule in his own right. Eurydice later married Ptolemy, though if this was voluntary or not is unclear, though it ensured her remaining son's place in the line of succession. She also persuaded Iphicrates, an Athenian general who was adopted by Amyntas, to protect her sons against Pausanius, who was attempting a coup for the throne of Macedonia. This act was unprecedented act for a royal woman to seek foreign aid to protect the royal line of succession. Her plan was successful, with her second son, Perdiccas III avenging his brother's death and taking the throne, though this act led to Philip II being taken hostage by Thebes. Perdiccas over extended himself against Athens and was killed, leaving Philip II to eventually take control of the kingdom.
7 notes
·
View notes
Text
LiDAR reveals vast ancient Maya city and complex networks hidden in Mexico's Campeche forest
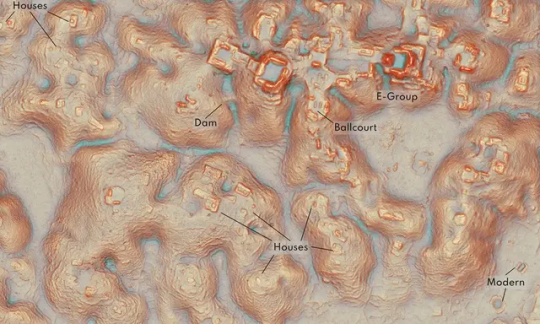
- By Nuadox Crew -
Archaeologists have uncovered thousands of ancient Maya structures and a large city named Valeriana in Campeche, Mexico, using aerial LiDAR technology to penetrate dense forest cover.
The discovery, which spans around 47 square miles, includes urban and rural settlements with reservoirs, temples, and roads, resembling other major Maya cities.
Previously overlooked due to its inaccessibility, Campeche is now recognized as a vital part of the Maya Lowlands, revealing complex urban planning and extensive connectivity among Maya cities.
The findings challenge the view of Maya cities as isolated entities, instead suggesting a vast, interconnected network.
Experts consider LiDAR a transformative tool, reshaping understanding of ancient Maya civilization and its environmental adaptation, organization, and conservation needs.
Image header: Core details of the Valeriana site. Credit: Luke Auld-Thomas et Al, Cambridge University Press.
Read more at CNN
Scientific paper: Auld-Thomas L, Canuto MA, Morlet AV, et al. Running out of empty space: environmental lidar and the crowded ancient landscape of Campeche, Mexico. Antiquity. 2024;98(401):1340-1358. doi:10.15184/aqy.2024.148
Other recent news
China Space Station Crew Returns to Earth: Three Chinese astronauts have returned to Earth after a six-month stay on the Tiangong space station.
Nvidia's Acquisition of Run:ai Faces EU Scrutiny: Nvidia will need to seek EU antitrust clearance for its proposed acquisition of AI startup Run:ai due to competition concerns.
Japan Launches Defense Satellite: Japan successfully launched a defense satellite using its new flagship H3 rocket, aimed at enhancing its military capabilities.
Global Smartphone Market Sees Best Quarter Since 2021: The global smartphone market has experienced its best quarter since 2021, partly due to Apple's new AI offering, Apple.
Indonesia Bans Google Pixel Sales: Indonesia has banned the sale of Google Pixel devices, just days after banning iPhone 16 sales, citing non-compliance with local investment rules.
Neuralink Rival Claims Vision Restoration: A rival company to Neuralink claims its eye implant has successfully restored vision in blind people.
#lidar#archaeology#paleontology#maya#history#china#space#nvidia#ai#smartphones#big tech#japan#satellite#defense#indonesia#google#ophthalmology#eye
11 notes
·
View notes
Text
Python for Beginners: Launch Your Tech Career with Coding Skills
Are you ready to launch your tech career but don’t know where to start? Learning Python is one of the best ways to break into the world of technology—even if you have zero coding experience.
In this guide, we’ll explore how Python for beginners can be your gateway to a rewarding career in software development, data science, automation, and more.
Why Python Is the Perfect Language for Beginners
Python has become the go-to programming language for beginners and professionals alike—and for good reason:
Simple syntax: Python reads like plain English, making it easy to learn.
High demand: Industries spanning the spectrum are actively seeking Python developers to fuel their technological advancements.
Versatile applications: Python's versatility shines as it powers everything from crafting websites to driving artificial intelligence and dissecting data.
Whether you want to become a software developer, data analyst, or AI engineer, Python lays the foundation.
What Can You Do With Python?
Python is not just a beginner language—it’s a career-building tool. Here are just a few career paths where Python is essential:
Web Development: Frameworks like Django and Flask make it easy to build powerful web applications. You can even enroll in a Python Course in Kochi to gain hands-on experience with real-world web projects.
Data Science & Analytics: For professionals tackling data analysis and visualization, the Python ecosystem, featuring powerhouses like Pandas, NumPy, and Matplotlib, sets the benchmark.
Machine Learning & AI: Spearheading advancements in artificial intelligence development, Python boasts powerful tools such as TensorFlow and scikit-learn.
Automation & Scripting: Simple yet effective Python scripts offer a pathway to amplified efficiency by automating routine workflows.
Cybersecurity & Networking: The application of Python is expanding into crucial domains such as ethical hacking, penetration testing, and the automation of network processes.
How to Get Started with Python
Starting your Python journey doesn't require a computer science degree. Success hinges on a focused commitment combined with a thoughtfully structured educational approach.
Step 1: Install Python
Download and install Python from python.org. It's free and available for all platforms.
Step 2: Choose an IDE
Use beginner-friendly tools like Thonny, PyCharm, or VS Code to write your code.
Step 3: Learn the Basics
Focus on:
Variables and data types
Conditional statements
Loops
Functions
Lists and dictionaries
If you prefer guided learning, a reputable Python Institute in Kochi can offer structured programs and mentorship to help you grasp core concepts efficiently.
Step 4: Build Projects
Learning by doing is key. Start small:
Build a calculator
Automate file organization
Create a to-do list app
As your skills grow, you can tackle more complex projects like data dashboards or web apps.
How Python Skills Can Boost Your Career
Adding Python to your resume instantly opens up new opportunities. Here's how it helps:
Higher employability: Python is one of the top 3 most in-demand programming languages.
Better salaries: Python developers earn competitive salaries across the globe.
Remote job opportunities: Many Python-related jobs are available remotely, offering flexibility.
Even if you're not aiming to be a full-time developer, Python skills can enhance careers in marketing, finance, research, and product management.
If you're serious about starting a career in tech, learning Python is the smartest first step you can take. It’s beginner-friendly, powerful, and widely used across industries.
Whether you're a student, job switcher, or just curious about programming, Python for beginners can unlock countless career opportunities. Invest time in learning today—and start building the future you want in tech.
Globally recognized as a premier educational hub, DataMites Institute delivers in-depth training programs across the pivotal fields of data science, artificial intelligence, and machine learning. They provide expert-led courses designed for both beginners and professionals aiming to boost their careers.
Python Modules Explained - Different Types and Functions - Python Tutorial
youtube
#python course#python training#python#learnpython#pythoncourseinindia#pythoncourseinkochi#pythoninstitute#python for data science#Youtube
3 notes
·
View notes
Text
Network Reconnaissance Tool AutoRecon for OSCP Penetration Testing
Are you tired of manually running countless enumeration commands during penetration testing or OSCP preparation? Let me introduce you to AutoRecon – a powerful multi-threaded network reconnaissance tool that will revolutionise your enumeration process. When tackling CTFs, OSCP labs, or real-world penetration testing engagements, efficient enumeration is crucial. However, manual enumeration can be…
#autorecon#CTF#enumeration tools#ethical hacking#information gathering#network reconnaissance#OSCP#penetration testing#recon automation#Tib3rius
0 notes
Text
Class Feature Friday: Obliteration Faculty (Nanocyte Faculty)

(Render of the Service Weapon as it appears in its Grip form in the game Control by Remedy Studios)
There’s a lot of fun things about the nanocyte class, and there are just so many fun ways to use nanites in and out of combat.
Perhaps one of their most offensive abilities is the ability to create weapons from their symbiotic nanites, giving them powerful tools of destruction they can never truly be disarmed of.
For today’s entry, however, we’ll be looking at a variant of the nanocyte that specializes in destruction using such created weapons. They might provide advanced targeting to pinpoint the most lethal areas of a target’s body, or they might reshape the weapon on the micro-scale to be even more lethal , or even sacrifice droves of their components to enhance the damage in other ways.
No matter the exact method, not only do these nanocytes become especially lethal against their targets, but they can use their methodology to spread the harm to other targets as well, becoming nanomachine-enhanced engines of destruction.
The weapons these warriors create are built to let nothing stop them, penetrating hard materials and even altering to accept a little extra charge (or nanite surge) to become more damaging, the latter by imbuing nanites into the projectiles or striking area for extra damage.
The nanites can even sacrifice themselves to imbue the weapon with other types of damage, superheating themselves or chilling for fire or cold, or overloading for electricity.
Whether they are left behind by a melee weapon or are carried to the target at range, these nanocytes can discharge such nanites that they spray out from the wound, carrying the form of damage to a nearby target to spread destruction, though it is naturally lighter than the initial impact.
Additionally, the guidance of their nanites makes them more accurate when attacking repeatedly.
Later on, their sprays of nanites can spread further and with an expenditure of nanites can be used repeatedly in the same onslaught of attacks.
Naturally, a nanocyte with this faculty is going to primarily be using their gear array to create weapons, as all of their faculty abilities center around such weapons. They typically only would use their sheath array when out of combat for the protective benefits and the cloud when avoidance is more important than fighting. As such, their knacks are going to be mostly made up of those that enhance their weapons or otherwise make them more effective combatants, such as heavy armor edge, material alterations, split manifestation, eldritch upgrade, heavy weapon edge, and so on. In either case, you can build them as either melee or ranged attackers with ease, or perhaps split your focus.
With their destructive abilities, the nanites bonded to these nanocytes almost certainly had an origin in combat, meant to enhance the performance of both the host and their equipment. Of course, even if that is true, the character might not have been the intended recipient. In such a case, the nanites might simply be continuing their function, or they might have adapted such combat potential as a solution for keeping their host alive and safe in a hostile environment.
Seeking information about a former client, the party singles out a xulgath member of a mercenary company who is known for being a drunken partyer. Getting him to talk should be easy, but if he discovers the ruse he’ll prove to be a dangerous combatant, his intoxication doing nothing to hamper the nanites in his body.
Rumor has it that a magitech-focused corporation is developing a method of creating hybrid magitech nanites able to enhance the host with magically-empowered attacks. In order to do so, they’ve been studying stolen aeon stone network constructs to see how each component coordinates with the others. However, they don’t realize the risk when one collection gets free and attempts to merge with the others to create a powerful distress signal relay.
Valgoth the Arsenal is an infamous pirate, named for the vast array of heavy weapons his nanites can replicate and enhance. They say he was once a super soldier serving in some warlike nation’s military, but it appears that for some reason or another, he left, choosing to ply his skills in taking from merchant vessels.
10 notes
·
View notes
Text
Fuel Your Growth with Performance Marketing
Turn clicks into customers with laser-focused strategies and real-time results.

Introduction: Marketing That Delivers, Not Just Promises
In today’s fast-paced digital landscape, businesses no longer have the luxury of spending blindly on ads and waiting for miracles. What they need is performance marketing—a results-driven approach that focuses on conversions, not just impressions. It's data-backed, ROI-focused, and scalable, making it the future of modern marketing.
🎯 What is Performance Marketing?
Performance marketing is a digital strategy where advertisers pay only for measurable results—be it clicks, leads, sales, or app installs. Unlike traditional branding methods, performance marketing demands proof. Every campaign is trackable, every rupee spent is accountable.
Key components include:
Pay-Per-Click (PPC) advertising
Affiliate marketing
Social media paid campaigns
Native and display ads
Retargeting & programmatic advertising
💡 Why Businesses Love Performance Marketing
Performance marketing offers powerful benefits for brands across industries:
✅ Cost-Effective – No upfront lump sums; pay only for outcomes ✅ Trackable & Transparent – Live dashboards show real-time performance ✅ Highly Targeted – Reach only your ideal audience with pinpoint accuracy ✅ Scalable – Start small, test, and grow based on results ✅ Optimized for ROI – Every ad is backed by metrics that matter
From startups to big brands, everyone wants results—and this strategy delivers.
📈 Lead Generation: The Lifeline of Sales
No leads = no business. Performance marketing supercharges your sales funnel with high-quality, intent-driven leads across platforms:
Google Search & Display Network
Meta (Facebook/Instagram) Ads
LinkedIn for B2B targeting
YouTube & OTT for awareness-based targeting
Landing pages with integrated lead capture forms
By using tools like A/B testing, heatmaps, and behavioral tracking, marketers ensure that visitors convert—not just click.
🔧 Tools & Techniques that Drive Results
The magic lies in optimization. A great campaign uses:
Advanced analytics (Google Analytics, Meta Pixel, UTM tracking)
Retargeting to re-engage bounced traffic
Conversion Rate Optimization (CRO) for better lead quality
Funnel building with precise customer journeys
AI and automation for budget control and ad performance
When campaigns are backed by smart data, results are not left to chance.
🧠 Who Should Use Performance Marketing?
E-commerce brands looking to scale sales
Startups wanting fast market penetration
Service-based businesses aiming for qualified leads
Real estate, education, fintech, and healthcare sectors for niche targeting
Agencies managing multiple client portfolios
🌟 Final Word: Measure More. Waste Less.
Marketing budgets are shrinking, but expectations are growing. Performance marketing strikes the perfect balance by focusing only on what works. It’s not about shouting louder—it’s about reaching smarter.
🔗 Ready to generate real leads and real growth?
Start your performance marketing journey today!
👉 [Click Here] to explore high-ROI digital strategies!
2 notes
·
View notes
Text
DUST FROM THE PAST: CHAPTER 3 KITH AND KIN
She was a transfer. She’d been the only one. The rhythmic vibrations of the semi-truck's engine reverberated through the container, each jolt and sway causing her to slide involuntarily against the unyielding walls. Her stabilizers, impaired by the sedation, struggled to maintain equilibrium, amplifying her disorientation.
The darkness inside the crate was absolute, her visual sensors unable to penetrate the sealed environment. Auditory inputs were limited to the muffled hum of the truck's engine and the occasional hiss of air brakes, each sound a reminder of her uncertain journey. Her internal chronometer, though functioning, offered little comfort as time seemed to stretch interminably.
Despite the sedation, fragments of operational protocols surfaced in her neural network, but they provided no context for her current situation. A semblance of apprehension, an emergent property of her adaptive algorithms, coursed through her circuits—a response not entirely unlike fear.
As the miles passed, the monotony of motion became a constant, lulling her into a state of passive observation. Yet, beneath the surface, her processors remained active, analyzing and reanalyzing data in an attempt to make sense of her predicament. The uncertainty of her destination and purpose loomed over her consciousness, casting a shadow over her synthetic mind.
Darkness. A thick, suffocating kind. Junebug’s reboot cycle dragged her back from the void in slow, aching increments. She wasn’t sure how long she’d been out, her internal clock flickered erratically, struggling to regain stability. For a moment, everything was pure static, her sensors feeding her nothing but corrupted noise. Then– sensation hit. Her limbs felt detached, like she was floating just outside of herself. Her servos stuttered as power sluggishly returned, creeping through her artificial system like ice thawing. The dull weight of her body settled in first, her back pressing against something solid and cold. Her optics flickered, a weak attempt at waking up. It took her a moment to register that she’d been drooling. She forced herself to be patient, letting her systems recalibrate as her auditory sensors crackled back to life. The room was quiet—too quiet. Not the kind of silence that meant peace, but the kind that meant absence. Emptiness. A space abandoned. Bit by bit, the static in her head cleared. The air smelled of old oil and dust, thick with the scent of metal long since corroded, but beneath it was something more familiar. The ghost of a memory—burnt circuits, soldered wires, the sharp bite of coolant fluid. She knew this place. Not in the way she knew the shape of a wrench in her hand or the hum of the bike engine running smooth, this was deeper, instinctive. A place she hadn't visited in years, locked away in her memory. Her workshop. No, not hers. Not anymore. Her wrists twitched, the movement met with sharp resistance. Cold steel bit into her plating, snug around her right wrist, her left moved freely. A chain, looped around the workbench’s sturdy frame, anchoring her in place. Junebug exhaled sharply, rolling onto her side. Her joints protested, servos stiff from inactivity, but she forced herself to move. She tugged at the restraint, testing the length of the chain. Not much slack. Just enough to stand. Her optics swept the room, cataloging details. It wasn’t exactly how she left it, but the bones were the same—her old workbench, the scattered tools, the cracked concrete floors stained with grease. A familiar suffocating weight settled in her chest, a sensation she thought she’d escaped when she left this place behind. She swallowed hard, her vents whirring softly to keep her systems cool. Then, without hesitation, she brought her restrained wrist to her mouth and sank her teeth into the chain, biting down hard. The chain didn’t budge. Her jaw ached, but she didn’t stop– wouldn’t stop. Then, footsteps.
A slow, deliberate rhythm against the concrete.
Junebug’s stopped mid-bite, her eyes snapping up to the door. A figure stood in the doorway, silhouetted by the flickering hallway light. The shape was unmistakable—familiar in a way that sent something cold curling through her core. And then they stepped forward. The light caught sleek, polished plating, reflecting off a frame nearly identical to her own. Taller, sharper. Their eyes gleamed an unnatural shade of gold, cold and assessing. Vex. Vexamortis. Her twin. Not by choice. Not by bond. By design. Vex clicked their tongue, arms folding across their chest as they took in the sight before her. "Really, June?" The name dripped from her tongue, mocking. "Didn’t take you for the animalistic type. Biting through steel? That’s just sad." Junebug didn’t answer, didn’t move. Her grip on the chain tightened, just for a second. Vex stepped closer, casual in their cruelty, head tilting slightly. "But I guess it fits, doesn’t it? You always were more stray than sister." Junebug’s vents hitched, but she forced herself to stay still. No reaction. No tells. She knew how Vex worked—how they picked at old wounds just to watch them bleed. Vex crouched down, meeting her gaze as she forcefully grabbed Junebug’s chin.
"You should’ve stayed gone."
⚙︎・•● ● •・⚙︎ Consciousness returned in waves, sluggish and uneven, like surf dragging over jagged rock. Johnny’s processors stuttered back online, his internal systems sluggish from the lingering effects of the EMP. Static hummed at the edges of his thoughts, his limbs distant, unresponsive. The first thing he registered was the cold.
It seeped into him through the floor, biting where his plating met the concrete. His internal temperature regulation flickered, fighting between warmth and chill, never quite settling.
He tried to move—his fingers twitched, his servos whirring weakly—but something was pulling against him. He wasn’t free.
A rattle. A sharp tug against his wrist. His optics flickered fully online, pupils adjusting to the dim, industrial glow overhead. Chains. Heavy, thickly linked, running from his wrist to the floor. He took a breath he didn’t need. Voices registered next low murmurs, casual conversation, Laughter– sharp, biting. Not kind. He sluggishly turned his head, vision unblurring, and then he registered the other body in the room. Tempest leaned against a rusted bench, arms folded. Surge, lounging against the wall, smirked like she was waiting for a punchline to a joke only she understood. There were others, newer faces, among the ones he hadn’t seen in years. PB, smaller than the rest, perched on a crate, bouncing one knee with restless energy. Her optics gleamed with barely contained excitement, a manic edge to her grin. Alani, silent, unreadable, sat on the edge of a table, watching with something closer to curiosity than cruelty. Churchill and Rex—massive, looming figures—flanked either side of the room, their presence a wall in itself. It was a reunion. Johnny swallowed down the static fuzzing at the edges of his mind, forcing himself upright as much as the chain would allow. His wrists ached where the metal links dug in, but he ignored it, scanning the room again. No Junebug. That was the first thing he noted, and it tightened something in his chest. Tempest must’ve caught the flicker of emotion across his face, because he let out a quiet chuckle, pushing off the workbench.
“Looking for someone?” His voice was smooth, edged with something that made Johnny’s circuits bristle.
Johnny flexed his fingers, testing how much give the chain had. Not much. “Where is she?” His voice came out hoarse, like it had been scraped raw.
Surge clicked her tongue, stepping forward with exaggerated leisure. “Aw, listen to him. Just woke up and already asking questions.” She crouched in front of him, her optics gleaming in the dim light. “Didn’t anyone ever tell you to mind your manners?”
Johnny barely flinched when she reached out, tapping a clawed finger under his chin. He stared back at her, unwilling to give her the satisfaction of a reaction.
“She’s alive,” Alani said from the table, her voice smooth, neutral. “For now.”
Something in Johnny’s chest uncoiled just slightly—but not enough. Not when he was still chained to the floor, surrounded. PB’s grin widened. “You should be thanking us, you know. Could’ve left you both scrapped in a ditch. But nah, we’re generous.” She rocked back on the crate, looking far too pleased with herself. “Figured we’d catch up first.” Johnny’s hands curled into fists. “Catching up.” He tested the words, flat and empty. “That what we’re calling it?”
Surge tilted her head. “Well, I suppose it depends on what you think we owe each other.” She stood, placing a foot on his chain and pressing down—not enough to hurt, but enough to remind him exactly where he was. “You and Jamie—sorry, Junebug—walked out and never looked back. And we? We stayed. We rotted.” Her smirk widened, cruel. “And now we get to ask… was it worth it?”
Johnny set his jaw, his vents hissing slightly as his systems worked through the tension. “You want an apology?” He met Surge’s gaze, unflinching. “Ain’t got one.”
Churchill let out a low chuckle, arms crossed. “Feisty for someone chained to the floor.”
Johnny didn’t break eye contact with Surge, but he could feel Tempest moving closer.
“See, here’s the thing,” Tempest murmured, his voice softer now, more measured. He crouched slightly, getting to Johnny’s level, his expression unreadable. “You might think you don’t owe us anything. That running was the right call. But we’ve had years to think about it.” He reached out, tapping the side of Johnny’s head, almost gentle. “And I don’t think you’ve had enough time to think.”
Johnny’s optics flickered, his limbs tensing.
“We’ll fix that.” Tempest stood, nodding to Surge.
Before Johnny could react, Surge crouched fast, gripping his chin between her fingers, forcing him to look at her. “But hey, maybe I was wrong,” she said, mock-sweet. “Maybe you do want to catch up.”
Then she leaned in close, her smirk sharp.
“Lucky you, Johnny. You’re not going anywhere.” The room fell into a weighted silence as Tempest straightened, rolling his shoulders with an air of quiet control. His presence alone was enough to command attention, but the way the others instinctively shifted, the way their focus turned toward him, made it clear—he was the one in charge here. Johnny had always known Tempest carried a certain weight among them, even back in the mines. But this was different. This wasn’t the old hierarchy of survival, the unspoken structure of laborers and those who kept them in check. This was something sharper, more personal. When Tempest finally spoke, his voice was low, measured. “I think you’re under the impression that you still have choices, Johnny.” He stepped forward, his boots scraping against the floor as he closed the distance between them. “Let me clear that up for you.”
Johnny’s jaw tightened, but he stayed quiet, watching
“You don’t talk unless we let you talk.” Tempest crouched slightly, his expression unreadable as he studied Johnny’s face. “You don’t move unless we let you move.” He lifted a hand, gripping the chain binding Johnny’s wrist and giving it a sharp tug, just enough to jolt him off balance. Johnny barely caught himself, his optics flickering.
“You don’t breathe unless we decide it’s worth our time.”
The words settled like iron in the air, and Johnny exhaled sharply through his vents. “That supposed to scare me?” His voice came out steady, but his fingers twitched slightly against the cold metal.
Tempest smiled, but there was no warmth in it. “No,” he said simply. “Just making sure we understand each other.”
Surge let out a quiet chuckle from behind him. “And here I was thinking we’d have to break him in slow.”
Tempest ignored her. He stood fully, his shadow falling over Johnny as he released the chain and took a step back. “You’ve been gone a long time,” he said, almost conversational. “Maybe you forgot how things work around here. But you’ll remember soon enough.”
Johnny flexed his fingers again, his optics darting toward the door before settling back on Tempest. “Where’s Junebug?”
For a second, Tempest said nothing. Then, with an exhale, he turned, “You really wanna see your little girlfriend that badly? Alright then, let’s go.” Tempest didn’t look at Johnny as he spoke again, but his voice was final. “Don’t make me regret it.”
⚙︎・•● ● •・⚙︎ The room was dim, the overhead lights humming faintly as Johnny was led forward. The chain binding him to Tempest clinked softly with each step, a quiet, insistent reminder that he wasn’t walking freely.
Surge moved ahead, her stride loose and easy, like she had nothing to fear, nothing to hurry for. PB trailed behind, practically vibrating with energy, grinning like she was getting away with something.
Johnny barely noticed them. His mind was fixed ahead—on the door, on what waited beyond it.
Tempest said nothing as he pushed it open. The hinges groaned, the stale air inside rolling over them like a breath from something long asleep. Johnny’s optics adjusted instantly, sharpening against the dim glow of a single flickering light. Junebug was there.
She was slumped against a workbench, one wrist bound to it by a heavy, industrial chain. Her frame sagged with forced stillness, but she was upright—awake. Her optics, dulled but still burning blue, flicked up at the sound of movement.
Johnny felt something in his chest tighten.
“June,” he breathed She blinked sluggishly, recognition taking a second too long to register. When it did, something in her posture shifted—too slight for anyone but him to notice.
Behind him, Tempest gave a small, humorless chuckle. “See? She’s fine.”
Johnny barely heard him. He stepped forward, only to be yanked back by the chain.
Junebug’s optics flickered toward the movement. She took in the restraint, the way Johnny was being escorted rather than simply let in. Her jaw tightened.
“I’m fine,” she said, voice rough.
A lie. Johnny exhaled sharply, forcing down the growing coil of frustration in his gut. “They hurt you?”
Junebug’s fingers twitched against the workbench, but she didn’t answer. That was answer enough.
Tempest made a low, amused sound. “Alright, alright,” he drawled. “You’ve had your moment. Time’s up.”
Johnny turned sharply, yanking against the chain as he faced Tempest. “Give us a minute.”
Tempest just smiled, a slow, deliberate thing. “I did.”
Before Johnny could argue, the chain was pulled tight, jerking him backward toward the door.
Junebug moved then—just a fraction, just enough to lean forward against the restraint on her wrist. “Johnny—”
He twisted against Tempest’s grip, trying to hold onto the sight of her, trying to carve her into memory before they forced him away.
“June—”
The door slammed shut between them.
⚙︎・•● ● •・⚙︎ The door’s heavy slam sent a dull vibration through the workshop, rattling loose screws on the workbench. The sound lingered in the air, stretching thin over the quiet hum of the overhead lights.
Junebug sat motionless, staring at the door as if sheer will alone could pull Johnny back through it.
Then she moved.
Her fingers curled into a slow, deliberate fist, servos whirring as she tested the strength left in her limbs. The chain around her wrist was thick—industrial-grade, bolted into the workbench like a part of the machinery itself. She gave it an experimental pull, teeth grinding as the restraint barely shifted.
Her optics flickered toward the room. It was almost her old workshop—the same sterile walls, the same workbenches lined with half-finished projects and scattered tools. But it wasn’t hers.
Not anymore.
A slow, controlled breath. Her systems ran a diagnostic, struggling to recalibrate after the EMP had left her sluggish and off-balance. The echo of Johnny’s voice lingered in her audio logs, overlapping with the last time she’d seen him before everything went black.
June—
She flexed her fingers again, eyes narrowing.
They’d brought her here for a reason.
They weren’t done with her yet.
3 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes